Hack The Box: Busqueda
In this writeup, I’ll be sharing my experience solving the Hack The Box (HTB) challenge called “Busqueda”. I’ll walk you through my process, the tools I used, and how I overcame the obstacles in this challenge. I’ll also include screenshots to illustrate the steps.

Overview
Briefly describe the “Busqueda” challenge, including its difficulty level and the skills required to solve it.
Reconnaissance
In this section, I’ll discuss the initial reconnaissance phase, including the tools and techniques I used to gather information about the target system.
Scanning and Enumeration
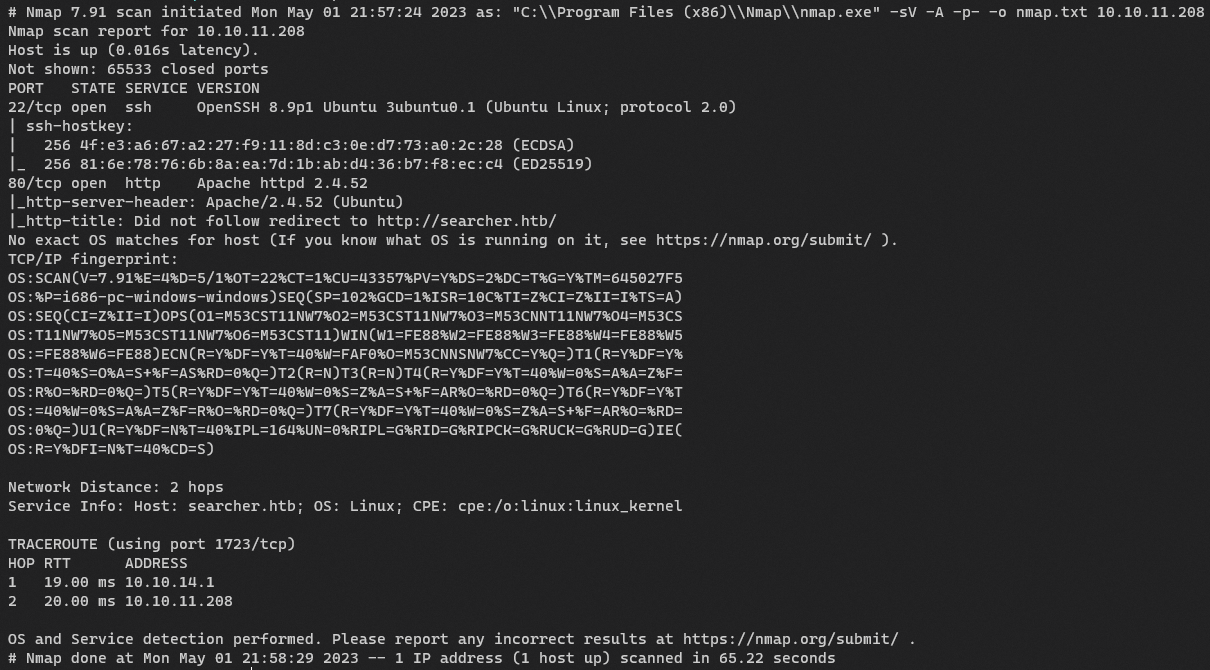
Include a description of how you performed scanning and enumeration. Mention the tools you used (e.g., Nmap, Dirbuster) and the results you obtained.
Identifying Vulnerabilities
Explain how you identified potential vulnerabilities in the target system, such as outdated software or misconfigurations.
Exploitation
In this section, I’ll walk you through the steps I took to exploit the identified vulnerabilities and gain access to the target system.
Gaining Initial Access
Describe the process of gaining initial access, including the tools and techniques you used (e.g., Metasploit, manual exploitation). Add relevant screenshots.

Privilege Escalation
Explain how you escalated your privileges on the target system, including the tools and techniques you used (e.g., searching for credentials, exploiting misconfigurations). Add relevant screenshots.

Post-Exploitation
In this section, I’ll discuss what I did after gaining full access to the target system, such as finding flags, exploring the system, and cleaning up.
Capturing the Flags
Explain how you captured the user and root flags, and add screenshots of the flags.


Lessons Learned
Summarize the main takeaways from this challenge, including new skills, techniques, or tools you learned.
I hope you enjoyed this writeup about the “Busqueda” HTB challenge. Stay tuned for more Hack The Box writeups and cybersecurity content!